Blog
Embrace a Zero Trust policy with Microsoft Azure
The enhanced pace of digital transformation has prompted organizations to migrate their workloads to a secure cloud platform. Organizations also require a more versatile security model, that accommodates the modern-day working environment, while ensuring multilayered data protection.
Microsoft’s Zero Trust Framework protects assets anywhere by adhering to three principles:
- Verify explicitly: Always authenticate, based on the available data points, including user identity, device health, anomalies, workload, and data classification.
- Use least privileged access: Limit user-access with just-in-time and just-enough-access (JIT and JEA), risk-based adaptive policies, and data protection.
- Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, improve threat detection, and enhance defenses.
In this blog post, we will describe the main Azure network security services that help an organization to embrace Zero Trust, focusing on the third principle, ‘assume breach’.
Understand the Zero Trust model
The Zero Trust model ensures that every access request is fully authenticated before access is granted. In other words, it secures an organization by eliminating implicit trust and continuously validating each stage of a digital interaction. It is based on analytics and intelligence to identify anomalies in real-time, offering added security to all corners of the enterprise
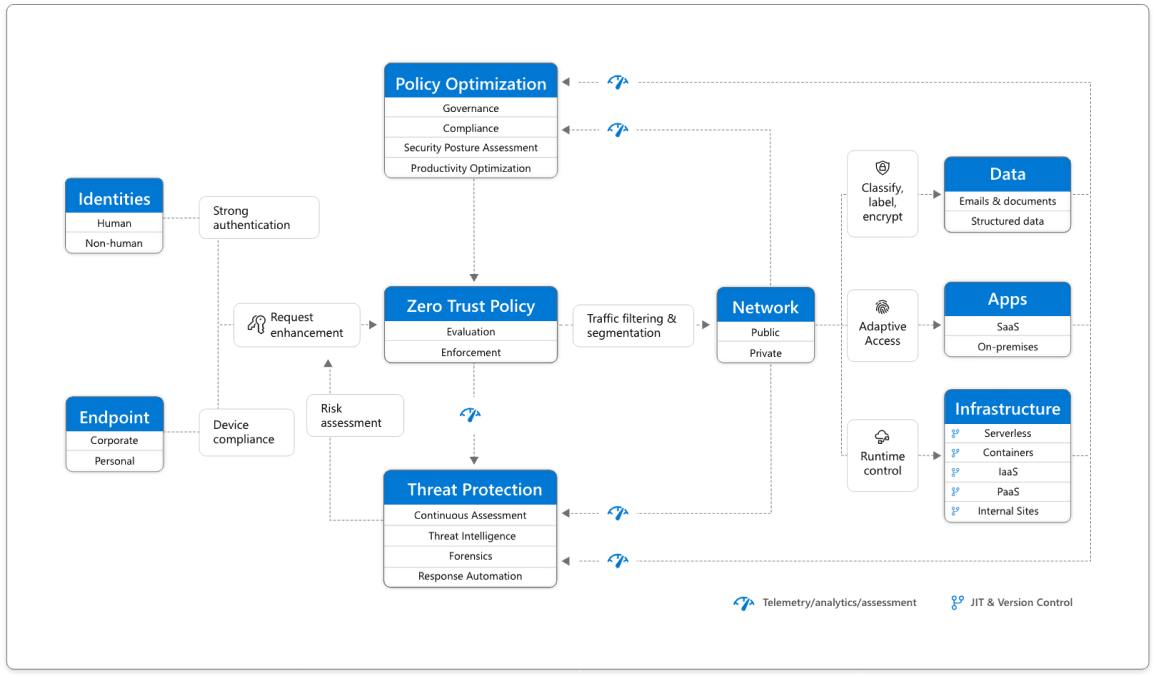
This strategic approach to security should extend to your entire digital estate, including identities, endpoints, apps, as well as infrastructure. The Zero Trust framework serves as an end-to-end strategy, with integration across all elements.
The foundation of Zero Trust is identity. Both human and non-human identities need to be authenticated, authorized, and validated to maintain access to applications and data. It involves connecting from personal or corporate endpoints, from a compliant device and requesting access based on Zero Trust principles.
As a unified policy enforcement, requests are intercepted and explicitly verified across six foundational elements before access is granted. These signals include the role of the user, their location, device compliance, data sensitivity, application sensitivity, and much more. In addition to telemetry and state information, the risk assessment from threat protection feeds into the policy engine, to automatically respond to threats in real-time. The policy is enforced at the time of access and is continually evaluated throughout the session.
This policy is further enhanced by Policy Optimization. Governance and compliance are critical to a strong Zero Trust implementation. Security Posture Assessment and Productivity Optimization are necessary to measure the telemetry throughout systems.
The telemetry and analytics feed into the Threat Protection system. Large amounts of telemetry and analytics, enriched by threat intelligence, generate high-quality risk assessments that can be manually investigated or automated. As cyber-attacks happen at cloud speed, defense systems must act at the same pace. Humans simply cannot sift through all the potential risks quickly enough to eliminate all possible threats. The risk assessment feeds into the policy engine for real-time automated threat protection, and additional manual investigation, if needed.
Traffic filtering is applied to the evaluation and enforcement of the Zero Trust policy, before access is granted to any network. Data classification and encryption should be applied to internal chats, emails, documents, and structured data. As per Microsoft, access to applications should be adaptive - whether SaaS or on-premises. Runtime control is applied to infrastructure, with serverless, containers, IaaS, PaaS, and internal sites, with just-in-time (JIT) and Version Controls actively engaged.
Lastly, telemetry, analytics, and assessment from the network, data, application, and Infrastructure are fed back into the Policy Optimization and Threat Protection systems.